Be careful. New platforms invite bad actors.


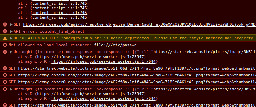
Found the error Not allowed to load local resource: file:///etc/passwd while looking at infosec.pub's communities page. There's a community called "ignore me" that adds a few image tags trying to steal your passwd file.
You have to be extremely poorly configured for this to work, but the red flags you see should keep you on your toes for the red flags you don't.
You are viewing a single comment
Holy shit this is kind of unsettling. Though I would expect ALL major browsers to reject reading any local files like this..... would this kind of thing actually succeed somewhere/somehow?
If you ran your browser as root and configured your browser to load local resources on non-local domains maybe. I think you can do that in chrome://flags but you have to explicitly list the domains allowed to do it.
I'm hoping this is just a bad joke.
you don't need to be root to read
/etc/passwdThat’s because passwd doesn’t store the password hashes. Just user names.
Are you sure? What do you get when you run
$ cat /etc/passwdin terminal? Just paste the results here 😇Edit: to anyone reading this on the future, don't actually do this, it was a joke
yup pretty sure
😉
Weird, all I see is *******
[This comment has been deleted by an automated system]
Yeah, seems highly unlikely to ever yield any results. Even if you did manage to read a file, you have to get lucky finding a password hash in a rainbow table or the password being shit enough to crack.
Also generally the actual password (or rather its hash) is stored in /etc/shadow on most systems from the past 20 odd years.