Lemmy.ml tankie censorship problem



Pro tip: set a 40 minute timer on your phone as soon as you put the beer in the freezer.
I remember when I got my first computer with 1GB of RAM, where my previous computer had 64MB, later upgraded to 192MB. And there were only like 3 or 4 years in between them.
It was like: holy shit, now I can put all the things in RAM. I will never run out.
There was a guy named Jesus that was crucified by the romans and all that. There is proof of that
There isn't actually. The proof is basically: it's embarassing that their cult leader got painfully crucified, so the early Christians and writers of the new testament wouldn't have made that shit up.
Personally I find it rather unconvincing.
Just don’t compain that YouTube doesn’t play 4K videos anymore.
strange, mpv handles it just fine
The point is that your example use case of "YouTube 4k videos" doesn't need a browser full of bloated js garbage.
Actually lot less than the browser. Under 300MB, I just checked, and that's mostly just the network buffer which is 150MB by default.


People be like:

Yeah god forbid people have some interesting discussion on this platform, right?
Trim support is standard. Any kernel released in the past 15 years or so will have trim support built in. So that's not something you should worry about.
How trimming is triggered is another matter, and is distro dependent. On Arch and Debian at least there is a weekly systemd timer that runs the fstrim command on all trimmable filesystems. You can check it if's enabled with: systemctl list-unit-files fstrim.timer. I can't tell how other distributions handle that. On Debian derived ones, I imagine it's similar, on something like Slackware, which is systemd-less and more hands-off in its approach, you may have to schedule fstrim yourself, or run it manually occasionally.
There is also the discard mount option that you can add in /etc/fstab, which enables automatic synchronous trimming every time blocks are deleted, but its use is discouraged because it carries a performance penalty.
Hope that answers your question.
They're just going to do a classical boil-the-frog operation:
I'm not sure how they accomplish that
If they have database access, which they would have being the admins, they can do anything.
But emoji's are not derived from the Simpsons. They're derived from the yellow smiley face ideogram that originated in the 1960s, it was designed by the artist Harvey Ball.
It's yellow, not because it's supposed to represent whiteness, but because the company colors of the State Mutual Life Assurance Company it was designed for were yellow and black, and because it feels sunny, bright and positive. It's an anthropomorphized representation of the Sun, and does not represent a human with a specific skin color.

I think unlike on hexbear and lemmygrad, most lemmy.ml users simply don't know, and many communities hosted there are bona fide. I'm not throwing stones at them, it's the admins of the instance that I have a beef with.
Who made Red Hat the arbiter of when xorg should end?
I mean, sure they're a major Linux vendor but their market is servers with hardly any foothold in the desktop market. It would be more interesting to see how long Debian, Ubuntu or Arch will keep xorg alive.
So how does that work given that most Steam games are x86/x64 and the M2 is an ARM processor? Does it emulate an x86 CPU? Isn't that slow, given that it's an entirely different architecture, or is there some kind of secret sauce?
Using double NAT here because my ISP won't even support/allow putting their box in bridge mode and I don't even have root access to it, just some limited functionality via their web GUI.
I haven't had any issues with it.
Realistically it's not super dangerous, and no you probably don't have a virus just from browsing a few tech support sites, but you do eliminate your last line of defense when you run software as root. As you know, root can read/change/delete anything on your system whereas regular users are generally restricted to their own data. So if there is a security problem in the software, it's made worse by the fact that you were running it as root.
You are right though that Firefox does still have its own protections - it's probably one of the most hardened pieces of software on your computer exactly because it connects to the whole wide internet - and those protections are not negated by running as root. However if those protections fail, the attacker has the keys to the kingdom rather than just a sizable chunk of the kingdom.
To put that in perspective though, if there is a Firefox exploit and a hacker gets access to your regular user account, that's already pretty bad in itself. Even if you run as a regular unprivileged user they would still have have access to things like: your personal documents, your ssh keys, your Firefox profile with your browsing history, your session cookies and your saved passwords, your e-mail, your paypal account, your banking information, ...
As root, they could obviously do even more like damage like reading all users' data, installing a keylogger or screengrabber, installing a rootkit to make themselves undetectable, but for most regular users most of the damage is already done when their own account is compromised.
So when these discussions come up, I always have to think about this XKCD comic:
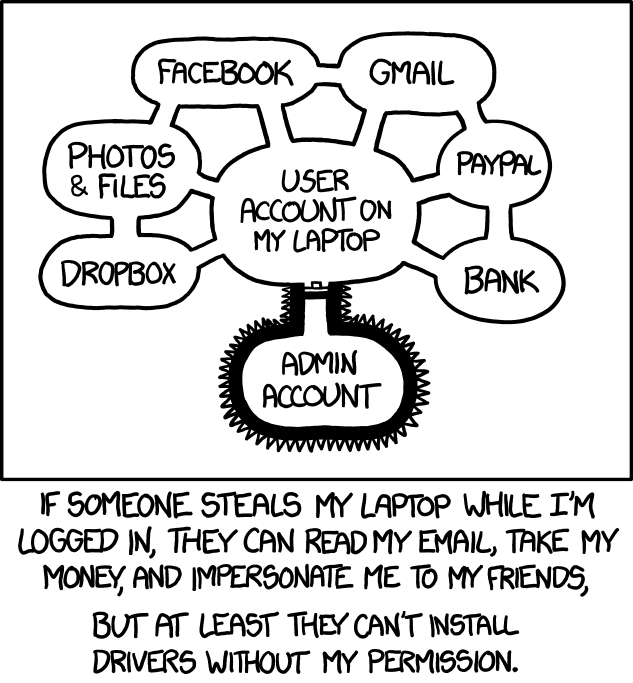
Yeah there goes my coffee ...
Another difference is that on forums you tend to get to know the members if you hang around long enough. On reddit/lemmy I never got this feeling, you're just discussing with random usernames and once the discussion is over, you will probably never run into each other again.
The post doesn't answer the questions, it's why I asked.
It says:
All running on a krun microVM with FEX and full TSO support 💪
I was not expecting Party Animals to run! That's a DX11 game, running with the classic WineD3D on our OpenGL 4.6 driver!
Now I know some of these words, but it does not answer my question.
And rightly so. There's a reason we're migrating away from pulse to pipewire.
For the longest time the solution to any audio issues was "just uninstall PulseAudio, and use plain ALSA", and that usually worked. I held out for years and ran an ALSA only setup because it just worked and PulseAudio was always giving me one issue or another (audio lag, crackling, unexplained muting), until some applications started to drop ALSA support.
Then Pipewire came along, and so far it has been rock solid for me.
Just use rsync -va
NO STOP!
The default quick check algorithm of rsync is not safe for this. It only checks filesize and modification time to determine if files are equal. After a b0rked copy, these are not to be trusted.
You should add the -c flag so that files are properly checksummed, unfortunately if you have slow storage on either end, this often negates the speed advantage of rsync.
For example, consider this example:
mkdir source
mkdir destination
echo "hello" > source/file.txt
echo "world" > destination/file.txt
touch -r source/file.txt destination/file.txt
rsync -avh source/ destination/
cat source/file.txt
cat destination/file.txt
Contrary to what you might expect, the rsync command copies nothing and the output at the end will show:
hello
world
If you change the rsync command in the example above to rsync -c -avh source/ destination/, it will work as expected.
I gotta say, it's working. I pirate a lot less than a few years ago. Not because I'm afraid of getting sued, but because it's all shite not worth pirating nowadays.
The attack surface will be a systemd daemon running with UID=0 instead, because how else are you going to hand out root privileges?
So it doesn't really change anything to the attack surface, it just moves it to a different location.
The UI is fine.
It's just that Github is a code sharing and collaboration platform for developers, not a software package distribution platform for end users.
In the fallout, we learn a little bit about mental health in open source.
Reminded me of this, relevant as always, xkcd:
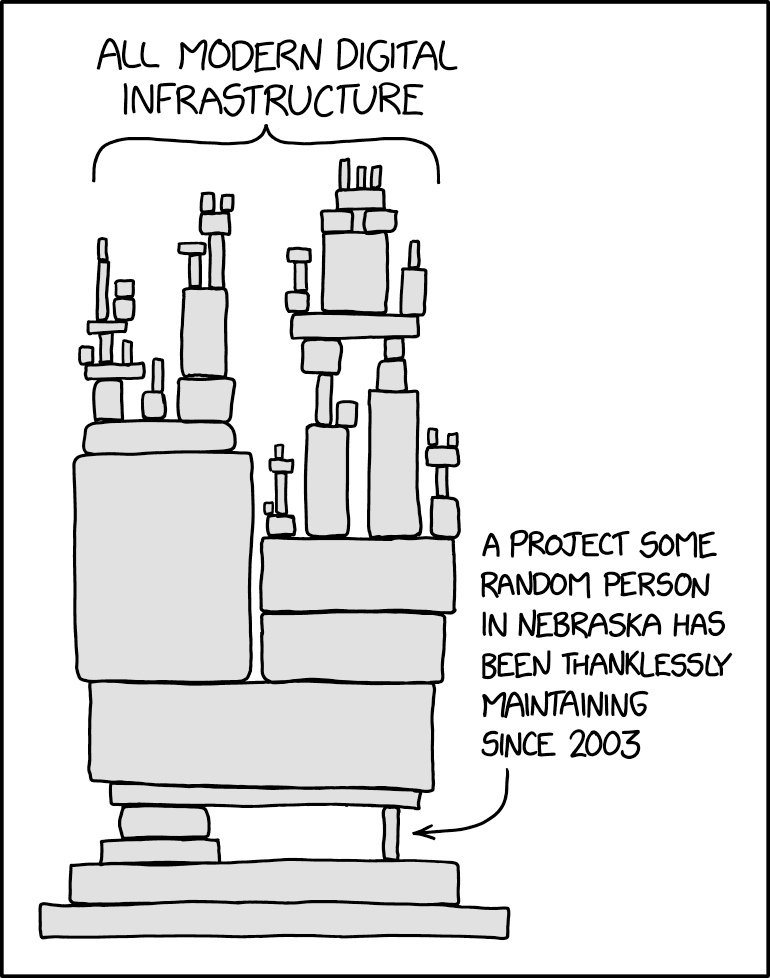
My big take away is that social media as we know it is likely generational
I don't think that's the right takeaway. The demographics of certain platforms may be skewed, but people who for example were active on Facebook 10 years ago still exist, they're just posting a lot less.
I think engagement is down across the board because of various reasons: the continuing crappification of the various platforms, people are starting to realize the risks of oversharing and public sharing, people are getting turned off about loud toxic discussion, people are becoming aware that their data is being mined by faceless corporations who don't have their best interest in mind, in short all the negatives of these platforms have become more obvious to the average user.
When people tell you to use Linux, they're not telling you that to solve your immediate problem (e.g. your "show desktop" icon has been replaced with a different icon), but they are telling you to get out of your abusive relationship with Microsoft, because that is the real problem: Microsoft does not respect you, the end-user of their product, and this kind of abusive shit will keep happening for as long as you keep using Windows.
I don't want to change back, but I still thought it added a sense of adventure, and having to be actively involved with the navigation gave you more awareness of where you were and where you were going. Now you just slavishly follow instructions and then some hours later you are there.
Like, we drove to Austria last summer and when we came back my dad asked me: so did you drive over Stuttgart or Nuremberg? And I honestly didn't know.
Living in the bubble of "CCP did nothing wrong (and we will ban you from all your favorite communities if you dare to disagree)" isn't exactly a great alternative.
It was a company almost from the start. In the mid 90s Tatu Ylonen created ssh v1 and released it as freeware, then shortly afterwards apparently he regretted it and created ssh v2, made it proprietary and commercialized it with his company.
In the late 90s some OpenBSD guys then forked the unencumbered ssh v1 source to create OpenSSH and implemented ssh v2 with it and their ssh version eventually gained traction and became dominant.
Yeah, but for example !linux@lemmy.ml is the only reasonably active community on Linux, and one of the communities I frequent the most.
You're welcome, cunt
Maybe not everyone is a native English speaker who can sense the difference in nuance in contemporary usage between words which are essentially synonyms.
And "Good Times" by Edie Brickell, but for some reason nobody ever remembers that lol
India, Pakistan, China: ...
You left out an important part.
In most Western countries, air has been getting consistently cleaner the past decades due to increasingly strict regulation.
You do need to know it when you're working with subnets and routing tables.
Unless you have anything but a flat network structure with everything in one subnet, working with IPV6 is a giant PITA.
clients (apps) should continue to use the PulseAudio/JACK APIs because the PipeWire API is not designed for general use
Really? That is news to me ... explains why mpv's pipewire audio output was briefly broken a couple of months ago.
You may also want to check if your bios is up-to-date.
My 5900x had some spontaneous crashes and reboots when I just got it, a bios update eventually resolved it. This was around the time zen3 was just out, and there were still quite a few bugs in AMD's AGESA library, which is included in the motherboard's bios.
Many motherboards still ship with an ancient bios, or just have been sitting on a shelf somewher for a very long time with an old bios. So if you have never touched your bios, check that first.
Exactly. That would be like using a web browser made by Google so they have direct access to your internet browsing history. Ridiculous!