Basically they fucked up and don’t like the criticism from other companies/ customers.
It's not really criticism, it's competitors claiming they will never fuck up.
Like, if you found mouse in your hamburger at McDonald's, that's a massive fuckup. If Burger King then started saying "you'll never find anything gross in Burger King food!" that would be both crass opportunism and patently false.
It's reasonable to criticize CrowdStrike. They fucked up huge. The incident was a fuckup, and creating an environment where one incident could cause total widespread failure was a systemic fuckup. And it's not even their first fuckup, just the most impactful and public.
But also Microsoft fucked up. And the clients, those who put all of their trust into Microsoft and CrowdStrike without regard to testing, backups, or redundancy, they fucked up, too. Delta shut down, cancelling 4,600 flights. American Airlines cancelled 43 flights, 10 of which would have been cancelled even without the outage.
Like, imagine if some diners at McDonald's connected their mouths to a chute that delivers pre-chewed food sight-unseen into their gullets, and then got mad when they fell ill from eating a mouse. Don't do that, not at any restaurant.
All that said, if you fuck up, you don't get to complain about your competitors being crass opportunists.
Even if that's the case, how is it Crowdstrike's place to call these other companies out for claiming something similar will never happen to them? Thus far, it had only ever happened to CS.
No, we had Sentinelone take down our company a few months ago. Granted, not a global outage, but it's something similar. I'm sure that if you went back in news archives, you'd find articles about major Sentinelone outages. I think Crowdstrike is just the biggest one in recent history. It's certainly not unprecedented.
It feels like a pattern though. I’ve not seen too much from them but they seem to be saying factually correct stuff. But neither worded correctly nor at the right time.
Even if that's the case, how is it Crowdstrike's place to call these other companies out for claiming something similar will never happen to them?
I agree completely, which is why I added that last sentence in an edit. This is a bad look for CrowdStrike, even if I agree with the sentiment.
Thus far, it had only ever happened to CS.
Everybody fucks up now and then. That's my point. It's why you shouldn't trust one company to automatically push security updates to critical production servers without either a testing environment or disaster recovery procedures in place.
I doubt you'll find any software company, or any company in any industry, that has not fucked up something really important. That's the nature of commerce. It's why many security protocols exist in the first place. If everyone could be trusted to do their jobs right 100% of the time, you would only need to worry about malicious attacks which make up only a small fraction of security incidents.
The difference here is that CrowdStrike sold a bunch of clients on the idea that they could be trusted to push security updates to production servers without trsting environments. I doubt they told Delta that they didn't need DRP or any redundancy, but either way, the failure was amplified by a collective technical debt that corporations
have been building into their budget sheets to pad their stock prices.
By all means, switch from CrowdStrike to a competitor. Or sue them for the loss of value resulting in their fuckup. Sort that out in the contracts and courts, because that's not my area. But we should all recognize that the lesson learned is not to switch to another threat prevention software company that won't fuck up. Such a company does not exist.
If you stub your toe, you don't start walking on your hands. You move the damn coffee table out of the pathway and watch where you're walking. The lesson is to invest in your infrastructure, build in redundancy, and protect your critical systems from shit like this.
Resiliency and security have a lot of layers. The crowd strike bungle was very bad but more than anything it shined a bright spot light on the fact that certain organizations IT orgs are just a house of cards waiting to get blown away.
I'm looking at Delta in particular. Airlines are a critical transportation service and to have issues with one software vendor bring your entire company screeching to a halt is nothing short of embarrassing.
If I were on the board, my first question would be, "where's our DRP and why was this situation not accounted for?"
House of cards is exactly right. At every IT job I've worked, the bosses want to check the DRP box as long as it costs as close to zero dollars as possible, and a day or two of 1-2 people writing it up. I do my best to cover my own ass, and regularly do actual restores, limit potential blast radii, and so on. But at a high level, bosses don't give AF about defense, they are always on offense (i.e. make more money faster).
This is the first time I've heard someone call it a house of cards and I think that fits it perfectly!
you'll never find anything gross in Burger King food!
Number fifteen...
That’s the first thing I heard in my head lmao
In what way did Microsoft fuck up? They don't control Crowdstrike updates. Short of the OS files being immutable it seems unlikely they can stop things like this.
Microsoft gave CrowdStrike unfettered access to push an update that can BSOD every Windows machine without a bypass or failsafe in place. That turned out to be a bad idea.
CrowdStrike pushed an errant update. Microsoft allowed a single errant update to cause an unrecoverable boot loop. CrowdStrike is the market leader in their sector and brings in hundreds of millions of dollars every year, but Microsoft is older than the internet and creates hundreds of billions of dollars. CrowdStrike was the primary cause, but Microsoft enabled the meltdown.
Microsoft did not "give Crowdstrike access to push updates". The IT departments of the companies did.
The security features that Crowdstrike has forces them to run in kernel-space, which means that they will have code running that can crash the OS. They crashed Debian in an almost identical way (forced boot loop) about a month before they did the same to Windows.
Yes, there are ways that Microsoft could rewrite the Windows kernel architecture to make it resistant to this type of failure. But I don't think there are very many other commercial OS's that could stop this from happening.
You're absolutely right, here is an in-depth explanation from Dave Plummer, the guy who wrote the task manager: https://youtu.be/ZHrayP-Y71Q
Microsoft gave CrowdStrike unfettered access to push an update that can BSOD every Windows machine without a bypass or failsafe in place. That turned out to be a bad idea.
Microsoft software licensing expert Rich Gibbons said: “Microsoft has received some criticism for the fact that a third party was able to affect Windows at such a deep technical level. It’s interesting that Microsoft has pointed out the fact this stems from a 2009 EU anti-competition ruling that means Microsoft must give other security companies the same access to the Windows kernel as they have themselves.”
Well there's a provocative anecdote if I've ever seen one. Well done.
It's not really criticism, it's competitors claiming they will never fuck up.
Not in all cases [podcast warning], sometimes it's just them pointing out they're doing silly things like how they test every update and don't let it out the door with <98% positive returns or having actual deployment rings instead of of yeeting an update to millions systems in less than an hour.
It's reasonable to criticize CrowdStrike. They fucked up huge. The incident was a fuckup, and creating an environment where one incident could cause total widespread failure was a systemic fuckup. And it's not even their first fuckup, just the most impactful and public.
Clownstrike deserves every bit of shit they're getting, and it amazes me that people are buying the bullshit they're selling. They had no real testing or quality control in place, because if that update had touched test windows boxes it would have tipped them over and they'd have actually known about it ahead of time. Fucking up is fine, we all do it. But when your core practices are that slap dash, bitching about criticism just brings more attention to how badly your processes are designed.
But also Microsoft fucked up.
How did Microsoft fuck up? Giving a security vender kernel access? Like they're obligated to from previous lawsuits?
And the clients, those who put all of their trust into Microsoft and CrowdStrike without regard to testing, backups, or redundancy, they fucked up, too
Customers can't test clownstrike updates ahead of time or in a nonprod environment, because clownstrike knows best lol.
Redundancy is not relevant here because what company is going to use different IDR products for primary and secondary tech stacks?
Backups are also not relevant (mostly) because it's quicker to remediate the problem than restore from backup (unless you had super regular DR snaps and enough resolution to roll back from before the problem.
IMO, clownstrike is the issue, and customers have only the slightest blame for using clownstrike and for not spending extra money on a second IDR on redundant stacks.
Classic corporate "leadership"
We didn't do nuffin shareholders, please pay
That one for sure...or: Here's a shiny new thing, customers. You didn't ask for it, and it actually makes our product a little bit worse...but it's new. You don't want to miss out on the new thing, do you?
Yeah, it was an international fuck up. You're going to get heat, and it's 100 percent deserved. Go cry in a corner and fuck off into oblivion.
It was called "Y2K if it happened".
Crowdstrike is a dead company now.
It's still embedded in a lot of machines.
They whine about this now, after they removed their “shady commentary” towards Microsoft from their website
Cry me a half billion dollar river, maybe we can use that money to fix all the damamges it did.
No, its good. They sent out $10 gift cards.
“Our industry is built on trust,” Sentonas said
And instead of following that statement with an apology to all the companies and people they royally fucked in the ass with their shitty business practices, they instead whined about other people pointing out what a massive, colossal, and completely preventable fuckup this was.
Good going sealing my resolve to never use crowdstrike.
Hey, they gave some people an Uber Eats coupon
A $10 UberEats voucher that most couldn't use
When TechCrunch checked the voucher, the Uber Eats page provided an error message that said the gift card “has been canceled by the issuing party and is no longer valid.”
So, fraud on to of everything else..? If they do some light treason, it's a hat trick!
Crowdstrike didn't just fuck up, they killed people. I personally had to postpone a blood test, but mine wasn't critical and I'm alive to complain. Not everyone is.
It's okay, they sent out $10 gift cards for Uber Eats to apologize (that they immediately cancelled).
To their customers*. Not to the literally billions of people directly affected by their debacle.
To their partners*. Which I believe are companies that help out with support or something.
imagine fucking uo so bad that uber dosen't allow you to use their gift cards
No, clowdstrike cancelled the cards after using them, if i understand correctly.
Awww, let's all feel bad for the rich, shitty company that has shitty quality control.
Hey, they're trying their hardest. It's hard because they had the joke build stored right next to the actual build so when they went to push it they clicked the wrong one.
I don't see the other companies fucking up so badly though.
That one recently with the 2.3 billion record data breach is pretty bad, and we collectively had no way to prevent it since it was through a private company.
You don't? Shit I see it all the time.
well, no, not at the level of taking down half the air traffic, police, ems, fire services, in the free world, you don't
Crowdstrike is far from the first company to ship bsod and bootloop bugs, they just happened to have the one that had the widest impact. Windows and it's ecosystem is buggy shit.
You see CrowdStrike level of bad all the time? Where? What? Who?
Equifax
Ok, and what else? I mean saying it happens all the time and listing one doesn't really prove the point.
That was super bad, and bad things like this do happen. Just saying it's all the time seems like it's really hyperbolic.
damn i haven’t used Windows in over a decade. are y’all ok?
Rofl, like Unix OSes never have problems. Even developers, who are among the most tech savvy users, tend to drag their feet on installing updates unless forced.
i was mostly making a joke about how this absolutely is not a common problem on any platform, not to this degree. and at least when my Arch and Nix systems go down i don’t have anyone to blame but myself. sure, systems have update issues, but a kernel level meltdown that requires a safe mode rescue? that’s literally never happened to me unless it was my fault
Even developers, who are among the most tech savvy users
Doubt
As a sysad, I’ll sign onto this.
Windows users are never OK.
Have you tried turning them off, then turning them on again?
Somebody should call them a wambulance since their fee-fees got hurt.
I do believe the number is still nine-wah-wah
In similar news, Enron says that people should stop being ambulance chasers by calling them out for corruption, fraud, and illegal activities.
ClownStrike had a massive, glaring issue with their main functionality that is THEIR COMPANY’S ONLY REASON FOR EXISTING that has been correctly attributed to criminally inept architecture decisions, no redundancy, no checks, no safety measures, and no accountability.
If I made the executive decision to design a system without any safety measures that could potentially push unchecked, malicious code to 90% of the computers that the business world runs on, I would be sued into dust. Honestly, if there were any justice in the world, the people at CrowdStrike that designed such a shite system should do actual prison time for their ineptitude.
If I made the executive decision to design a system without any safety measures that could potentially push unchecked, malicious code to 90% of the computers that the business world runs on, I would be sued into dust.
Or made a MS CEO....
/me glares at steve balmer
Sorry but some fields have no margin for error, just take the L and shut up.
Nah, this one has a margin of error. It's just that "take down a large percentage of all computers in the world simultaneously" is quite a bit outside of that margin for a security software.
I wonder if they'll end up doing a rename / rebrand if "ClownStrike" continues to haunt them (as it should).
If they do, I'm sure the new name will be some focus tested aberration they pay way too much for.
Yes 🤡
Youre a verb now, guys. That’s what happens when you fuck up that badly. Deal with it <3
make 8 million computers crash
other companies say you're trash
blame others
cry
They deserve to go bankrupt after that level of damage. I won't be surprised if a class action comes against them for gross negligence within the next few years. They're cooked and they know it.
Nothing shady about that commentary after seeing how they screwed up. I couldn't believe how amateur hour the cause of the crash was (the program not validating definition file contents, which spectacularly failed when fed a file consisting only of zeroes). They should rename themselves to ClownTrike.
That wasn't what was in the file, it was actual stuff. I saved a copy of it.
What happened was the file directed their craptastic snake oil software, which did absolutely no sanity checking first, to access memory it wasn't actually given which predictably resulted in it crashing, and since its dick was way up the kernels butt at the time they both went down together.
I've been calling them ClownStrike because they're clowns and their incompetence struck everyone else hard.
Yup a null pointer reference for a boot time driver. Which Microsoft never should've signed and should revoke. But ya know.... Money
Ah, thanks for the clarification on the details. Either way it boggles my mind that they didn't have checks in place.
Maybe you shouldn't have taken down half the world's airlines.
People do tend to notice shit like that.
Please proper nomanclature, clownstrike as in 🤡🤽♀️
And their customers are unhappy with the catastrophic service failure. Cry me a river.
I appreciated the RiskyBiz episode with the Sentinel one guys where they go over all the ways this could have been prevented if they did real testing
Crowdstrike absolutely deserves the shit they're getting.
Oh god. Sentinel one is horrible.
If they're taking issue with your testing, you've really screwed the pooch
Horrible how? I've always thought they were pretty solid in the arena.
Their ftrace hooks caused all disk usage to be serialized, making your multi-core processor single-core when doing anything I/O bound
We saw between 500% - 800% increases in build times with their software installed
Well, that's spectacular. What do you guys use now?
We're still using them on machines where performance doesn't matter
On build machines, they're on a special VLAN and don't have endpoint protection, but they only download from a protected mirror
We have a similar issue with defender, but those machines are internet connected, so we must have EDR on them.
Companies all over the world shutdown because of their incompetence. They do not deserve to be in the security business.
I think that's just called "living down an epic fuck up" but you know it's their company and they can cry if they want to.
Making millions, failing, causing global damage, then crying when people comment is quite nice and not at all hypocritical.
Did they try offering a $10 gift card to the other companies? "hah psyche!"
Womp womp, that's what happens when you shut down the global economy clownstrike
🤡💥
Well companies serve humans. Be better
Maybe you shouldn't have CRASHED THE FUCKING PLANET
Maybe you shouldn’t have PULLED A CROWDSTRIKE
FTFY
I am not in the knows about IT security at all, but isn't fucking up part of any security company? You can make shitty comments all you want but who says your company isn't the next one to fuck up?
Not wrong, but they fucked up due to incompetence, not just some random preventable accident.
From the technical details I've seen, just having a basic testing process/environment should have easily prevented this. That should be the bare minimum.
Ah, that changes things. A testing environment is pretty much the basics. You don't put untested things live.
Worry about the future of your stupid failure of a company, not your stupid feelings. Think of the feelings you've hurt over your stupid incompetence.
ah yes, strike the crowd, that'll help your reputation
Boo hoo, go fuck yourself.
We don't blame the leopards for eating faces. We blame the morons who let an external entity have control over their devices. And a clowd one at that.
I just wish they made it a feature, or something, cause I really dislike working and stuff
Basically they fucked up and don’t like the criticism from other companies/ customers.
It's not really criticism, it's competitors claiming they will never fuck up.
Like, if you found mouse in your hamburger at McDonald's, that's a massive fuckup. If Burger King then started saying "you'll never find anything gross in Burger King food!" that would be both crass opportunism and patently false.
It's reasonable to criticize CrowdStrike. They fucked up huge. The incident was a fuckup, and creating an environment where one incident could cause total widespread failure was a systemic fuckup. And it's not even their first fuckup, just the most impactful and public.
But also Microsoft fucked up. And the clients, those who put all of their trust into Microsoft and CrowdStrike without regard to testing, backups, or redundancy, they fucked up, too. Delta shut down, cancelling 4,600 flights. American Airlines cancelled 43 flights, 10 of which would have been cancelled even without the outage.
Like, imagine if some diners at McDonald's connected their mouths to a chute that delivers pre-chewed food sight-unseen into their gullets, and then got mad when they fell ill from eating a mouse. Don't do that, not at any restaurant.
All that said, if you fuck up, you don't get to complain about your competitors being crass opportunists.
Even if that's the case, how is it Crowdstrike's place to call these other companies out for claiming something similar will never happen to them? Thus far, it had only ever happened to CS.
No, we had Sentinelone take down our company a few months ago. Granted, not a global outage, but it's something similar. I'm sure that if you went back in news archives, you'd find articles about major Sentinelone outages. I think Crowdstrike is just the biggest one in recent history. It's certainly not unprecedented.
It feels like a pattern though. I’ve not seen too much from them but they seem to be saying factually correct stuff. But neither worded correctly nor at the right time.
I agree completely, which is why I added that last sentence in an edit. This is a bad look for CrowdStrike, even if I agree with the sentiment.
Everybody fucks up now and then. That's my point. It's why you shouldn't trust one company to automatically push security updates to critical production servers without either a testing environment or disaster recovery procedures in place.
I doubt you'll find any software company, or any company in any industry, that has not fucked up something really important. That's the nature of commerce. It's why many security protocols exist in the first place. If everyone could be trusted to do their jobs right 100% of the time, you would only need to worry about malicious attacks which make up only a small fraction of security incidents.
The difference here is that CrowdStrike sold a bunch of clients on the idea that they could be trusted to push security updates to production servers without trsting environments. I doubt they told Delta that they didn't need DRP or any redundancy, but either way, the failure was amplified by a collective technical debt that corporations have been building into their budget sheets to pad their stock prices.
By all means, switch from CrowdStrike to a competitor. Or sue them for the loss of value resulting in their fuckup. Sort that out in the contracts and courts, because that's not my area. But we should all recognize that the lesson learned is not to switch to another threat prevention software company that won't fuck up. Such a company does not exist.
If you stub your toe, you don't start walking on your hands. You move the damn coffee table out of the pathway and watch where you're walking. The lesson is to invest in your infrastructure, build in redundancy, and protect your critical systems from shit like this.
Resiliency and security have a lot of layers. The crowd strike bungle was very bad but more than anything it shined a bright spot light on the fact that certain organizations IT orgs are just a house of cards waiting to get blown away.
I'm looking at Delta in particular. Airlines are a critical transportation service and to have issues with one software vendor bring your entire company screeching to a halt is nothing short of embarrassing.
If I were on the board, my first question would be, "where's our DRP and why was this situation not accounted for?"
House of cards is exactly right. At every IT job I've worked, the bosses want to check the DRP box as long as it costs as close to zero dollars as possible, and a day or two of 1-2 people writing it up. I do my best to cover my own ass, and regularly do actual restores, limit potential blast radii, and so on. But at a high level, bosses don't give AF about defense, they are always on offense (i.e. make more money faster).
This is the first time I've heard someone call it a house of cards and I think that fits it perfectly!
Number fifteen...
That’s the first thing I heard in my head lmao
In what way did Microsoft fuck up? They don't control Crowdstrike updates. Short of the OS files being immutable it seems unlikely they can stop things like this.
Microsoft gave CrowdStrike unfettered access to push an update that can BSOD every Windows machine without a bypass or failsafe in place. That turned out to be a bad idea.
CrowdStrike pushed an errant update. Microsoft allowed a single errant update to cause an unrecoverable boot loop. CrowdStrike is the market leader in their sector and brings in hundreds of millions of dollars every year, but Microsoft is older than the internet and creates hundreds of billions of dollars. CrowdStrike was the primary cause, but Microsoft enabled the meltdown.
Microsoft did not "give Crowdstrike access to push updates". The IT departments of the companies did.
The security features that Crowdstrike has forces them to run in kernel-space, which means that they will have code running that can crash the OS. They crashed Debian in an almost identical way (forced boot loop) about a month before they did the same to Windows.
Yes, there are ways that Microsoft could rewrite the Windows kernel architecture to make it resistant to this type of failure. But I don't think there are very many other commercial OS's that could stop this from happening.
You're absolutely right, here is an in-depth explanation from Dave Plummer, the guy who wrote the task manager: https://youtu.be/ZHrayP-Y71Q
They have to give that access by EU ruling:
Well there's a provocative anecdote if I've ever seen one. Well done.
Not in all cases [podcast warning], sometimes it's just them pointing out they're doing silly things like how they test every update and don't let it out the door with <98% positive returns or having actual deployment rings instead of of yeeting an update to millions systems in less than an hour.
Clownstrike deserves every bit of shit they're getting, and it amazes me that people are buying the bullshit they're selling. They had no real testing or quality control in place, because if that update had touched test windows boxes it would have tipped them over and they'd have actually known about it ahead of time. Fucking up is fine, we all do it. But when your core practices are that slap dash, bitching about criticism just brings more attention to how badly your processes are designed.
How did Microsoft fuck up? Giving a security vender kernel access? Like they're obligated to from previous lawsuits?
Customers can't test clownstrike updates ahead of time or in a nonprod environment, because clownstrike knows best lol.
Redundancy is not relevant here because what company is going to use different IDR products for primary and secondary tech stacks?
Backups are also not relevant (mostly) because it's quicker to remediate the problem than restore from backup (unless you had super regular DR snaps and enough resolution to roll back from before the problem.
IMO, clownstrike is the issue, and customers have only the slightest blame for using clownstrike and for not spending extra money on a second IDR on redundant stacks.
Classic corporate "leadership"
We didn't do nuffin shareholders, please pay
That one for sure...or: Here's a shiny new thing, customers. You didn't ask for it, and it actually makes our product a little bit worse...but it's new. You don't want to miss out on the new thing, do you?
Yeah, it was an international fuck up. You're going to get heat, and it's 100 percent deserved. Go cry in a corner and fuck off into oblivion.
It was called "Y2K if it happened".
Crowdstrike is a dead company now.
It's still embedded in a lot of machines.
They whine about this now, after they removed their “shady commentary” towards Microsoft from their website
Reference: https://twitter.com/tomwarren/status/1816823026291270136
Cry me a half billion dollar river, maybe we can use that money to fix all the damamges it did.
No, its good. They sent out $10 gift cards.
And instead of following that statement with an apology to all the companies and people they royally fucked in the ass with their shitty business practices, they instead whined about other people pointing out what a massive, colossal, and completely preventable fuckup this was.
Good going sealing my resolve to never use crowdstrike.
Hey, they gave some people an Uber Eats coupon
A $10 UberEats voucher that most couldn't use
https://techcrunch.com/2024/07/24/crowdstrike-offers-a-10-apology-gift-card-to-say-sorry-for-outage/
So, fraud on to of everything else..? If they do some light treason, it's a hat trick!
Crowdstrike didn't just fuck up, they killed people. I personally had to postpone a blood test, but mine wasn't critical and I'm alive to complain. Not everyone is.
It's okay, they sent out $10 gift cards for Uber Eats to apologize (that they immediately cancelled).
To their customers*. Not to the literally billions of people directly affected by their debacle.
To their partners*. Which I believe are companies that help out with support or something.
imagine fucking uo so bad that uber dosen't allow you to use their gift cards
No, clowdstrike cancelled the cards after using them, if i understand correctly.
Awww, let's all feel bad for the rich, shitty company that has shitty quality control.
Hey, they're trying their hardest. It's hard because they had the joke build stored right next to the actual build so when they went to push it they clicked the wrong one.
I don't see the other companies fucking up so badly though.
That one recently with the 2.3 billion record data breach is pretty bad, and we collectively had no way to prevent it since it was through a private company.
You don't? Shit I see it all the time.
well, no, not at the level of taking down half the air traffic, police, ems, fire services, in the free world, you don't
Crowdstrike is far from the first company to ship bsod and bootloop bugs, they just happened to have the one that had the widest impact. Windows and it's ecosystem is buggy shit.
You see CrowdStrike level of bad all the time? Where? What? Who?
Equifax
Ok, and what else? I mean saying it happens all the time and listing one doesn't really prove the point.
That was super bad, and bad things like this do happen. Just saying it's all the time seems like it's really hyperbolic.
damn i haven’t used Windows in over a decade. are y’all ok?
Rofl, like Unix OSes never have problems. Even developers, who are among the most tech savvy users, tend to drag their feet on installing updates unless forced.
i was mostly making a joke about how this absolutely is not a common problem on any platform, not to this degree. and at least when my Arch and Nix systems go down i don’t have anyone to blame but myself. sure, systems have update issues, but a kernel level meltdown that requires a safe mode rescue? that’s literally never happened to me unless it was my fault
Doubt
As a sysad, I’ll sign onto this.
Windows users are never OK.
Have you tried turning them off, then turning them on again?
https://clownstrike.lol/
Lol perfect
Stahp, you meany!
CrowdStrike customers 'unhappy' with CrowdStrike
They lambasted Microsoft in their marketing materials but when others do it to them it's no fair? lol
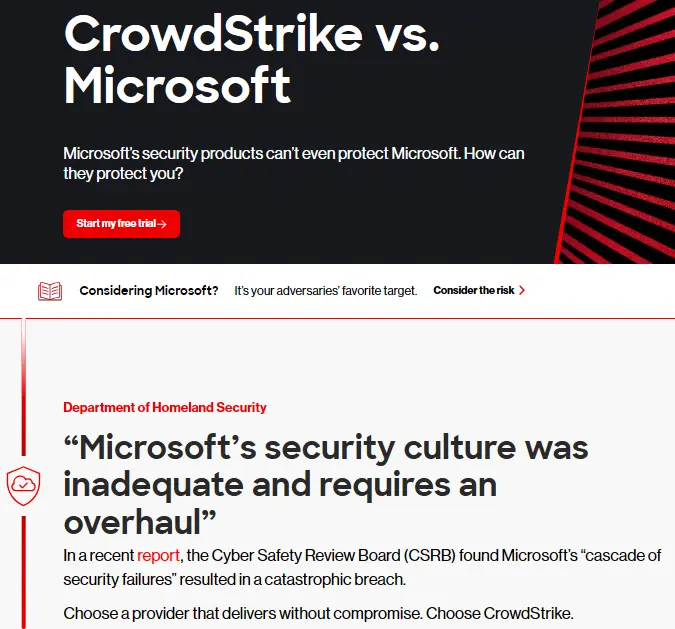
Compare the live page with the archive.
Looks like someone softened their language after the disaster, eh?
Looks like the difference between the two is that they removed the section calling Microsoft’s security culture inadequate.
I wonder what motivated the change.
Reminds me of this hahaha (~23 seconds in).
Somebody should call them a wambulance since their fee-fees got hurt.
I do believe the number is still nine-wah-wah
In similar news, Enron says that people should stop being ambulance chasers by calling them out for corruption, fraud, and illegal activities.
ClownStrike had a massive, glaring issue with their main functionality that is THEIR COMPANY’S ONLY REASON FOR EXISTING that has been correctly attributed to criminally inept architecture decisions, no redundancy, no checks, no safety measures, and no accountability.
If I made the executive decision to design a system without any safety measures that could potentially push unchecked, malicious code to 90% of the computers that the business world runs on, I would be sued into dust. Honestly, if there were any justice in the world, the people at CrowdStrike that designed such a shite system should do actual prison time for their ineptitude.
Or made a MS CEO....
/me glares at steve balmer
Sorry but some fields have no margin for error, just take the L and shut up.
Nah, this one has a margin of error. It's just that "take down a large percentage of all computers in the world simultaneously" is quite a bit outside of that margin for a security software.
I wonder if they'll end up doing a rename / rebrand if "ClownStrike" continues to haunt them (as it should).
If they do, I'm sure the new name will be some focus tested aberration they pay way too much for.
Yes 🤡
Youre a verb now, guys. That’s what happens when you fuck up that badly. Deal with it <3
They deserve to go bankrupt after that level of damage. I won't be surprised if a class action comes against them for gross negligence within the next few years. They're cooked and they know it.
Nothing shady about that commentary after seeing how they screwed up. I couldn't believe how amateur hour the cause of the crash was (the program not validating definition file contents, which spectacularly failed when fed a file consisting only of zeroes). They should rename themselves to ClownTrike.
That wasn't what was in the file, it was actual stuff. I saved a copy of it.
What happened was the file directed their craptastic snake oil software, which did absolutely no sanity checking first, to access memory it wasn't actually given which predictably resulted in it crashing, and since its dick was way up the kernels butt at the time they both went down together.
I've been calling them ClownStrike because they're clowns and their incompetence struck everyone else hard.
Yup a null pointer reference for a boot time driver. Which Microsoft never should've signed and should revoke. But ya know.... Money
Ah, thanks for the clarification on the details. Either way it boggles my mind that they didn't have checks in place.
Maybe you shouldn't have taken down half the world's airlines.
People do tend to notice shit like that.
Please proper nomanclature, clownstrike as in 🤡🤽♀️
And their customers are unhappy with the catastrophic service failure. Cry me a river.
I appreciated the RiskyBiz episode with the Sentinel one guys where they go over all the ways this could have been prevented if they did real testing
Crowdstrike absolutely deserves the shit they're getting.
Oh god. Sentinel one is horrible. If they're taking issue with your testing, you've really screwed the pooch
Horrible how? I've always thought they were pretty solid in the arena.
Their ftrace hooks caused all disk usage to be serialized, making your multi-core processor single-core when doing anything I/O bound
We saw between 500% - 800% increases in build times with their software installed
Well, that's spectacular. What do you guys use now?
We're still using them on machines where performance doesn't matter
On build machines, they're on a special VLAN and don't have endpoint protection, but they only download from a protected mirror
We have a similar issue with defender, but those machines are internet connected, so we must have EDR on them.
Companies all over the world shutdown because of their incompetence. They do not deserve to be in the security business.
I think that's just called "living down an epic fuck up" but you know it's their company and they can cry if they want to.
Making millions, failing, causing global damage, then crying when people comment is quite nice and not at all hypocritical.
Did they try offering a $10 gift card to the other companies? "hah psyche!"
Womp womp, that's what happens when you shut down the global economy clownstrike
🤡💥
Well companies serve humans. Be better
Maybe you shouldn't have CRASHED THE FUCKING PLANET
FTFY
I am not in the knows about IT security at all, but isn't fucking up part of any security company? You can make shitty comments all you want but who says your company isn't the next one to fuck up?
Not wrong, but they fucked up due to incompetence, not just some random preventable accident.
From the technical details I've seen, just having a basic testing process/environment should have easily prevented this. That should be the bare minimum.
Ah, that changes things. A testing environment is pretty much the basics. You don't put untested things live.
Worry about the future of your stupid failure of a company, not your stupid feelings. Think of the feelings you've hurt over your stupid incompetence.
ah yes, strike the crowd, that'll help your reputation
Boo hoo, go fuck yourself.
We don't blame the leopards for eating faces. We blame the morons who let an external entity have control over their devices. And a clowd one at that.
I just wish they made it a feature, or something, cause I really dislike working and stuff
so what, mental outlaw?